Solution Endpoint Detection & Response and Criticality
In recent years, cyber attacks have become more and more diverse in size and carried out in many different forms. Accompanied by advanced threats is constantly changing, adapting to overcome traditional defense systems based only on known patterns (signature) or some specific behavior, then invade. enter the organization / business system from there to silently perform dangerous acts such as hijacking, data theft or ransom … then they automatically delete the trace causing very many difficulties for the investigation process. The failure to fully grasp the evolution of an attack makes the organization / business have no plan to prevent if similar attacks occur in the future.
In the context of attackers increasingly using more sophisticated attacks that require organizations and businesses to equip themselves with solutions that are more detectable and responsive. Continuously monitoring and monitoring threats to provide visibility and contextualization so as not to miss important events is an extremely important requirement for incident detection and response.
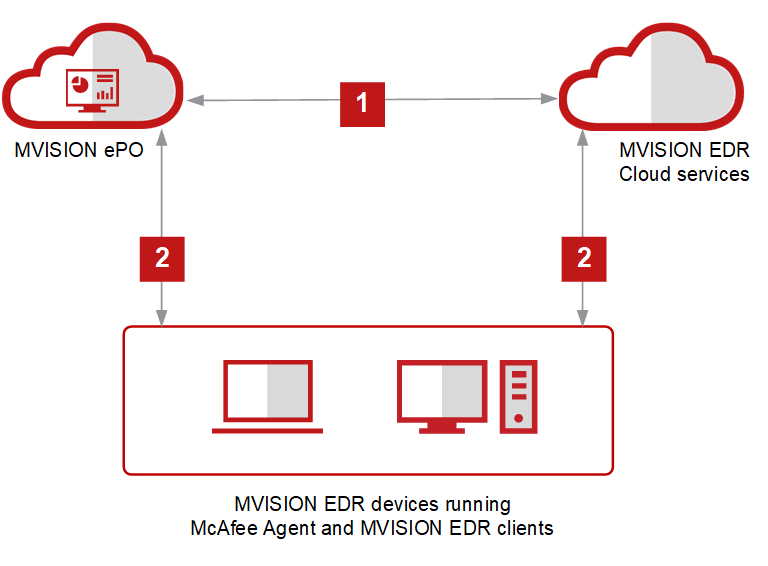
In order to meet the rigorous requirements in the context of increasingly demanding attacks, Endpoint Detection and Response (EDR) solution is capable of detecting advanced threats, the ability to Detailed investigation, and quick response. Continuously monitor and analyze in depth to early detect suspicious behaviors in the system. Using alert rating and data visualization methods to help administrators quickly identify threats and plan responses.
In addition, the EDR solution is capable of assisting organizations / businesses in reducing manpower and effort during investigation, speeding up analysis to quickly identify the root cause and risk of the incident.
The main features of the EDR solution:
| No | Policy/Task | Feature Description |
| 1 | Continuous real-time monitoring | Event information from user devices is continuously collected and monitored in real time. |
| 2 | Cloud-based analytics | The analyzer continually examines device activities to hunt for suspicious behavior and threats – from file attacks to file-less attacks. |
| 3 | MITRE ATT&CK™ mapping | Analytical results should be mapped with the MITRE ATT & CK ™ framework, supporting appropriate processes for detection of each threat session, associated hazards, and response priority. |
| 4 | Artificial intelligence guided investigation | The investigation guide builds on the expertise and experience of leading malware analysts with artificial intelligence (AI). These investigative guides make use of multiple hypothesis investigation and discovery processes for fast and accurate detection. |
| 5 | Broad data collection and local relevancy | The investigative machine incorporates artificial intelligence (AI) that gathers and processes the collected data to validate it into the alerts. These data are collected from many SIEM devices, systems … EDR solution compares the evidence with the normal activities of each organization / enterprise with collation with information sharing channels. other Threat Intelligence. |
| 6 | Flexible data display | The administrator can choose between many types of monitoring of the same data, from visualization to sorting and tabular display. |
| 7 | Search | Historical search: the ability to search the entire data stream collected from the devices. Analysts have the ability to search these data to see the breach index (IoC) and attack number (IoA) of the files even if these files have been deleted. |
| Real-time search: The ability to actively search allows the administrator to query information in real time. | ||
| On-demand data collection: to better support investigation, the solution has the ability to create a snapshot of the device, comprehensively collect the active processes, network connections, services. , and the autorun fields. |
INFORMATION ABOUT SOLUTION PROVIDER: