Security and Network Operation Center (SOC & NOC)


What is a Security Operations Center (SOC)?
The operation security center (SOC) is a place that houses an information security team (which is responsible for monitoring and analyzing the security posture of the organization) continuously. The SOC team aims to detect, analyze, and respond to network security incidents using a combination of technology solutions and a robust set of processes. Security operations centers are often staffed by analysts and engineers as well as supervising managers. SOC staff work closely with the organization’s incident response teams to ensure security issues are resolved quickly once discovered.
Security operations centers monitor and analyze activity across networks, servers, terminals, databases, apps, websites and other systems, looking for possible anomalies is a sign of a security problem or intrusion. The SOC is responsible for ensuring that potential security incidents are accurately identified, analyzed, protected, investigated and reported.
How does the Security Operations Center work?
Instead of focusing on developing a security strategy, designing a security architecture, or implementing safeguards, the SOC team is responsible for the continuing operational component of enterprise information security. The security operations center staff is composed mainly of security analysts working together to detect, analyze, respond to, report and prevent cybersecurity incidents. The additional capabilities of some SOCs may include advanced forensic analysis, cryptographic analysis, and malware reverse engineering to analyze the problems.
The first step in establishing an organization’s SOC is to clearly define a strategy that incorporates specific business goals from different departments as well as input and support from the executives. Once the strategy has been developed, the necessary infrastructure to support the strategy must be in place. According to Bit4Id Chief Information Security Officer Pierluigi Paganini, typical SOC infrastructure includes firewalls, IPS / IDS, breach detection solutions, exploration and event management systems and security information. honey (SIEM). Technology is needed to collect data through data streams, telemetry, packet capture, syslog and other methods so that data operation can be correlated and analyzed by SOC staff. The Security Operations Center also monitors networks and endpoints for vulnerabilities to protect sensitive data and comply with government or industry regulations.
What benefits will the SOC bring to the business / organization?
The main benefit of having a centralized operations hub is improved security incident detection through continuous monitoring and analysis of data activity. By analyzing this activity across the organization, the organization’s networks, endpoints, servers, and databases, SOC groups are critical to ensure timely detection and response to security incidents. confidential. The 24/7 monitoring provided by the SOC gives organizations an edge to protect against incidents and intrusions, regardless of the origin, timing or type of attack. The gap between attacker intrusion time and enterprise discovery time is huge, according to Verizon’s Data Breach Investigations Report. Having a secure operating center helps organizations bridge gaps and be proactive in dealing with threats.
Network Operations Centers (NOC) must have the following capabilities:
The Next-gen SIEM solution provides customers with a centralized storage and analysis system for logs and security events with an unprecedented, contextual correlation in the market.
Find out more
In addition to protecting the files and data in your computer, the sandbox also helps to limit the functionality of malicious code, authorizing certain code to have only certain functions, from there. cannot perform other interventions. The threat ransomware we see in most Hacker attacks, a Fortinet Advanced Threat Protection solution will combat and eliminate targeted attacks, coordinated through malicious software. scatter.
Find out more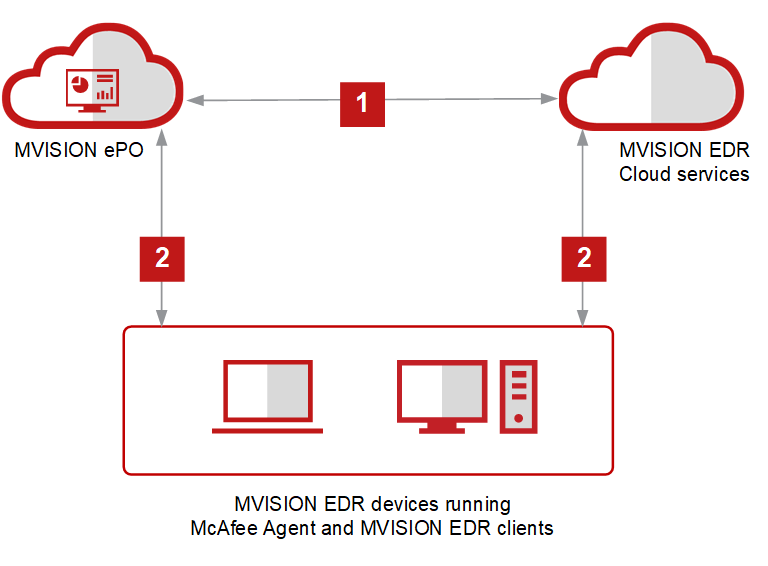
Endpoint Detection and Response (EDR) is an effective detection and response solution that finds advanced threats and eliminates them before they compromise data. Machine learning (both pre-execution and runtime), vulnerability protection, behavioral analysis, application control, and other advanced techniques designed to work seamlessly with endpoint protection your.
Find out moreTo avoid data breaches, businesses and organizations must detect and respond quickly to unusual activity. Entity and User Behavior Analysis (UEBA) can help you track down threats or behavior that alters user data, providing the ability to detect threats or other unauthorized influence on the system based on user behavior.
Find out more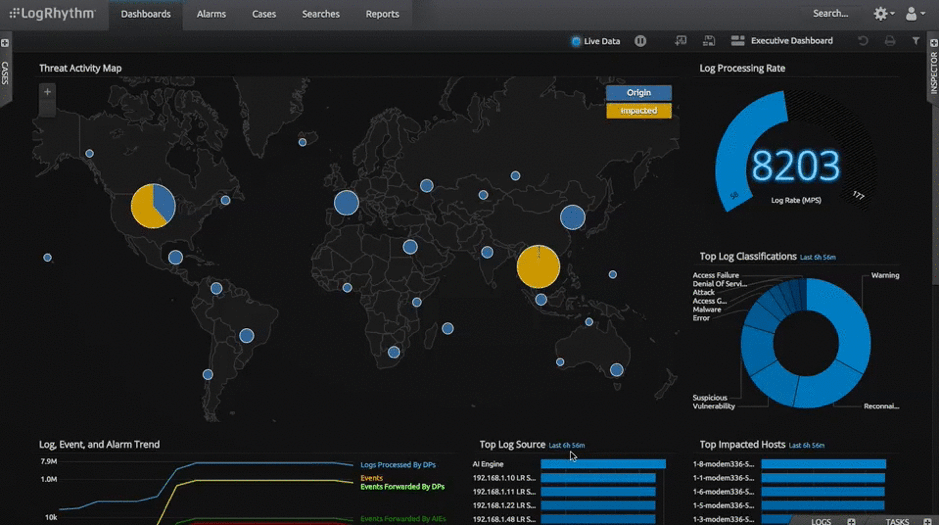

SOAR allows the aggregation of security solutions and security tools, allowing administrators to automatically collect data from any device, product or solution that is monitored by a suite. operations are secure and can identify problems and risks and provide responses to respective events, either automatically or manually.
Find out moreAdvanced Threat Defense (ATD) – McAfee’s zero day anti-malware sandboxing solution provides a set of analysis modules / engines to help analyze malware.
Find out more

With Network Detection and Response (NDR), ExtraHop provides perspective for you to understand your hybrid attack surface from the inside out. Our industry-leading network response and detection platform is built with the goal of helping you stay ahead of alert noise, silos, and flight technology so you can secure your future on the cloud. clouds.
Find out moreNetwork Performance Management and Diagnostics is the task of monitoring the performance of all network components at a granular level, in order to identify local performance bottlenecks and to ensure that the network can operate at a high level. performance as required and helps to reduce potential problems.
Find out more