Network Security
Network Security is a term that describes security tools, tactics, and policies designed to monitor, prevent, and respond to unauthorized network intrusions…
Find out moreSecurity and Network Operation Center
SOC & NOC is a total and flexible solution, provided on a basis to suit the current situation and security needs of the customer. This central system can help secure different endpoints.
Find out moreEndpoint Security
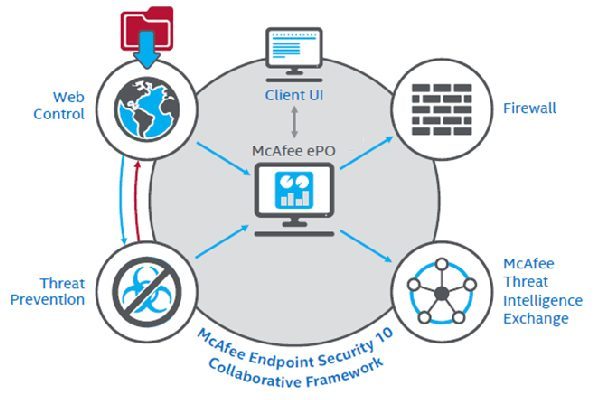
Endpoint Security is a proposed solution for endpoints, classified today by groups: workspaces, data centers, mobile devices or devices with specific functions.
Find out moreApplication Security
Application Security solutions describe application-level security measures to prevent data or code in the application from being stolen or hijacked. It includes the security considerations that occur…
Find our moreNetworks
Networks Solution – synthesizing a number of professional network security solutions such as ADC, Link Load Balancing, Wan Optimization and Tap & Network Packet Broker – supports optimal business in network connectivity and …
Find out moreNetwork and Security Testing
Network and Security Testing solution Identifies the risks of unauthorized theft of business data assets or leakage of sensitive information. Threat detection: Identify threats coming from inside or outside the corporate network through situational identification and proactive response.
Find out moreData Security
Data Security refers to the process of protecting data from unauthorized access and data corruption throughout its lifecycle. Data security includes data encryption, tokens, and key management practices that protect data across all apps and platforms.
Find out moreCloud Security
Cloud Security is a broad set of policies, technologies, applications, and controls used to protect virtual IP, data, applications, services, and related infrastructure of cloud computing.
Find out moreAccess Security
Access Security is a security technique that defines who or what can view or use a resource in a computing environment. It’s a fundamental concept in security that helps to minimize risk…
Find out moreSoftware & IoT
Software & IoT solutions include: 3D design with CAD / CAM with IoT solutions, virtual reality AR and integrated management software of PLM designs.
Find out more