Email Isolation
Email Security Status
Email isolation, email security is now considered an essential solution for businesses, Email is always a popular and easy way to attack a business through sending fake emails containing content. Malicious examples: attachments, links.
According to FBI estimates, email fraud is estimated to have damaged $ 675 million with 15670 incidents in 2017. Of which, about $ 3.1 billion were requested by cybercriminals to transfer via email using fake email. look for high-level positions. The total number of corporate email fraud cases nearly doubled from May to December last year, to 40,203 from 22,143.
According to statistics, in Vietnam, 96% of businesses use email as the main communication tool at work and the biggest problem that most businesses encounter is poor security email system, regular email. be interrupted, not receiving important messages as well as outgoing mail not reaching the recipient; often get spammed, or even
Regular mail security systems will rely on existing databases to identify attachments and links that are malicious or not and proceed to block them. However, the traditional approach will face some of the following disadvantages:
- For unique, unrecognizable content, it is not yet completely filtered.
- Malicious content included in attached links leads to a well rated website (corporate website hijacked), or applications hosted on Public Cloud (Google Drive, Dropbox, …).
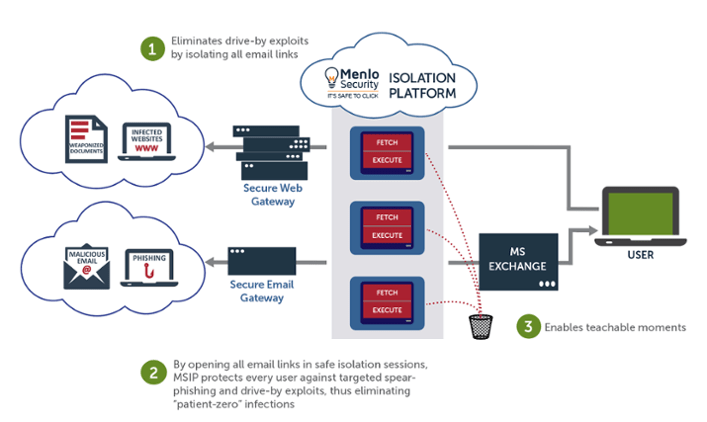
What can email isolation solution do?
Email isolation solutions help prevent cyber threats from entering users’ workstations through links contained in emails or attachments.
Integrating with Cloud Isolation Gateway system, email isolation solution will classify links and attachments in emails into 2 categories and have the following effects:
- Identified as malicious: Prohibits user access to confirmed malicious links and files
- No presence information: Conducted isolation on the Cloud Isolation Gateway component. Users will access attachments, direct links on the Cloud Isolation Gateway interface to completely isolate the links, the file directly accesses from the user’s workstation. From there, malicious components can not interfere and enter the workstation.
- Attachments are compressed and password-encrypted, making it difficult to analyze the contents.
Benefits of using an email isolation solution
Email isolation solution helps to protect users completely from email attacks. In addition, the email isolation solution still ensures users’ email experience.
Some uses:
- Supports integration with existing corporate email infrastructure, does not affect user experience.
- Isolate pages from links, attachments in emails. No malicious content can ever reach the workstation.
- Anti-malware and phishing.
- Protection against controlled infection, malicious ads and ransomware.
- Prevent C&C connections from malicious code and information exploitation.
- Supports filtering of encrypted files that contain passwords
- Statistics are informed access to malicious content of users in the system to support the operation and training of users about information security.
INFORMATION SOLUTION DISTRIBUTOR: