What is User and Entity Behavior Analytics?
To avoid data breaches, businesses and organizations must detect and respond quickly to unusual activity. Entity and User Behavior Analysis (UEBA) can help you track down threats or behavior that alters the user’s data, providing the ability to detect threats or other unauthorized influence on the system based on user behavior.
The importance of UEBA
Today, user-based threats are on the rise, risks associated with:
- Data theft incidents, internal impact.
- The breaches involve stolen or weakly secured credentials.
- Insider Threats
With UEBA, we can completely improve and correct the above problems by:
- Collect and enrich data from various sources for effective analysis.
- Get the most accurate view of the identity of a user or an entity.
- Detect known or unknown threats by applying advanced analysis.
- Speed testing and threat identification by correlating events and accessing underlying data fields directly.
- Standardize processes using Playbooks, Work-flow, and automate tasks based on the approval process.
- Using artificial intelligence (AI) and machine learning (ML) technologies to improve the time to detect and react to threats.
- Some key features of User and Entity Behavior Analytics
- Identify internal threats
Unintentional or intentional internal users cause damage, top network attacks and malicious acts to the system. This feature enhances monitoring, data auditing, policy violations, and other malicious activities.
Detecting hijacked accounts
Attackers will take advantage of and use the information of the compromised accounts. This feature helps distinguish between legitimate and hijacked account activity through a profile of learned behavior and anomalies detection. Discovers fake accounts before causing any damage.
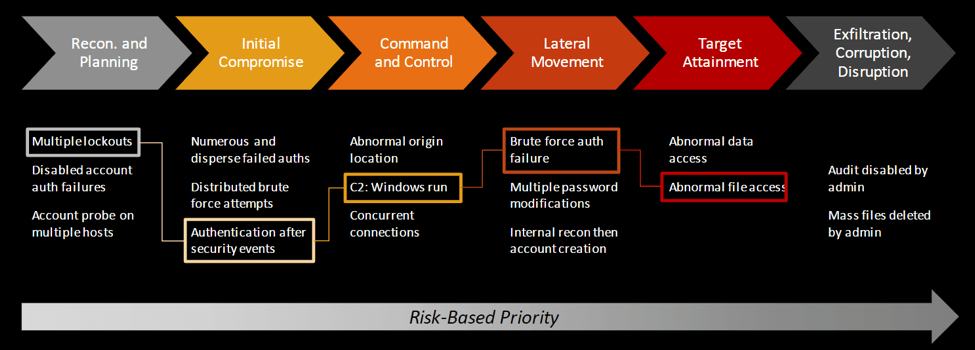
Detect abuse of privileges
Privileged users have all powers in the system, which is a great risk for organizations and enterprises. This feature tracks how privileged accounts are being used, by monitoring unauthorized new account creation, unauthorized access, and other risky activity.
Brute-Force attack
Attackers will target cloud infrastructure or external authentication systems. This feature provides advanced monitoring and provides fast, accurate warnings that help administrators stay one step ahead, quickly identify attacks and take countermeasures to block.
Track unauthorized access and data theft
When a user account is compromised or an internal tamper finds sensitive data, administrators need to promptly detect it. This feature comprehensively analyzes the file and monitors the data integrity (File Integrity Monitoring (FIM)), detecting improper user access to the data being protected in real time.
INFORMATION ABOUT PRODUCT DISTRIBUTORS: