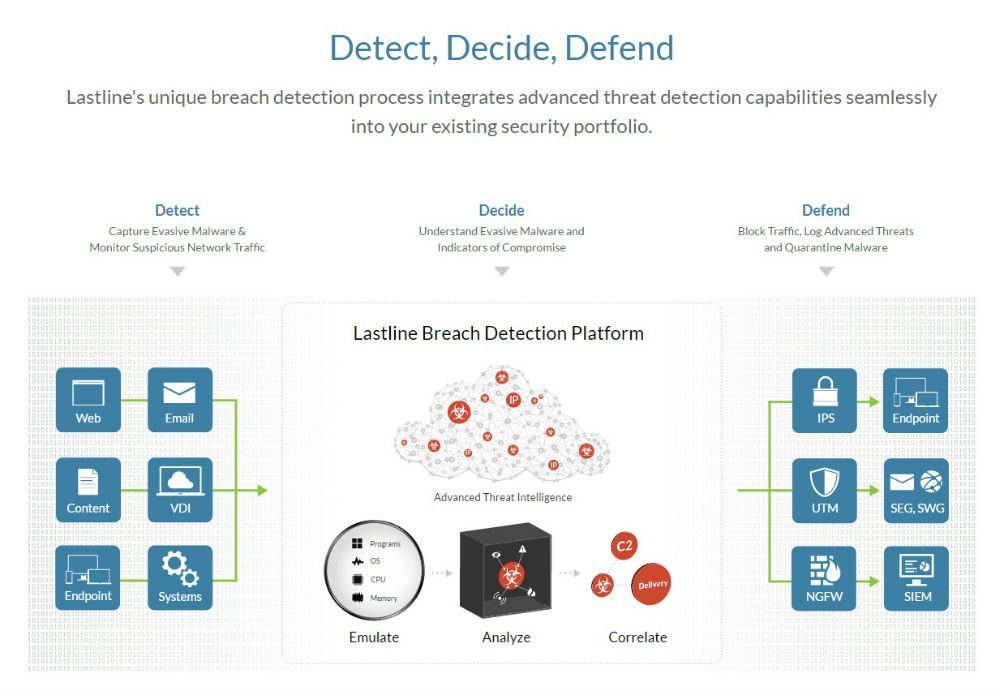
Discovery, Decision, Defense
Lastline’s unique intrusion detection technology was almost invisible when it was incorporated into customers’ existing security systems.
Covering the entire Business
All Covered
Protect all network nodes
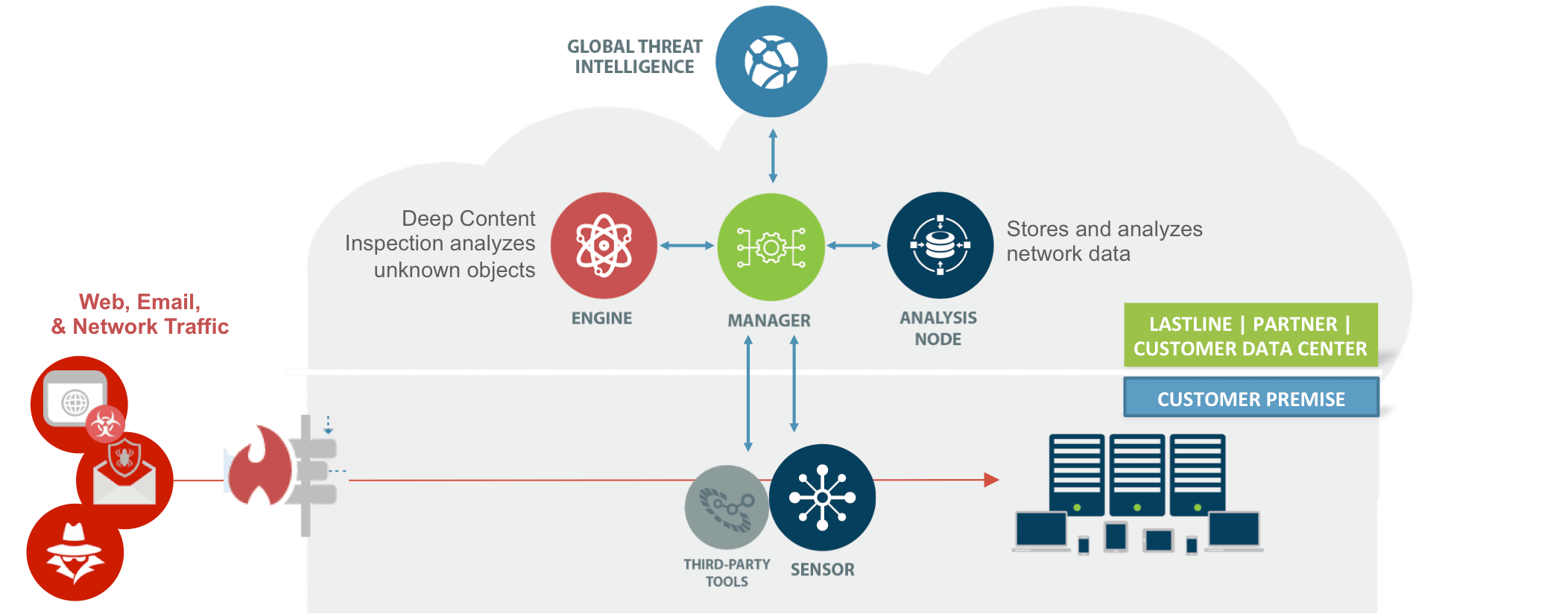
Lastline delivers comprehensive threat breach detection and lurks in the enterprise – works across different operating systems (Windows, Mac OS X, and Android), physical servers and virtualization, services, users, network infrastructure and Web applications, email, content, and mobile applications.
Deploy multiple Layers of Defense
Cover all physical or virtualized network systems
Strategic defense is not only on the outside but also in the data center, intranet, and distribution layers to increase security and prevent infection. Lastline software can be installed on physical servers, virtualization devices. Hence the deployment is easier than ever
Scalability is Predictable
Based on the number of users
Lastline’s flexible software platform allows organizations to scale defenses from a single point to unlimited expansion of representative offices, branches, mobile offices, etc. based on the number of users and not based on location, device or bandwidth.
Detects Anonymous threats that other devices
High Detection
With full system simulation
Lastline detects unknown threats (APTs, ATA, zero-day, …) designed specifically to evade from first generation APT sandbox equipment. When compared to other approaches such as operating system virtualization and emulation, Lastline’s system-wide emulation provides the deepest insight into the behavior of unknown malware at the same time. the hardest thing to get rid of anonymous malware. As a result, Lastline is able to detect anonymous malware that other solutions cannot.
Advanced Threat Intelligence
Be aware of the latest advanced malware
Lastline’s database contains advanced, anonymous malware information that no other security solution provider has, built on over 10 years of research and development. This database includes phantom servers (C&C), zero-day exploits, malicious websites, malicious code distribution points. With the ability to enter commands IDS / IPS, YARA, and intelligence technology to tailor the environment for analysis and defense from the threats that target your organization. This database is constantly being updated in coordination with partners and the customer environment.
Quickly detect Regardless of Bulk
Every second passes when you are under attack
The Lastline Breach Detection Platform identifies the key elements of intrusion for behavioral verification and relies on the database to trigger an incident response and immediate attack prevention. Dynamic analysis capabilities allow the new generation sandbox to adjust for changes in bandwidth without affecting the speed or integration of the analysis. Suspicious objects and traffic are analyzed in real time – not hours, minutes – providing the fastest possible notification and correction.
Respond to Advanced Attacks
Action Management
More signals, less noise
Analysis results are displayed on the web, using an event approach through evidence gathered from a new generation sandbox analysis system, network monitoring solution, and behavior detection. anomalous and correlated to analyze the action of ongoing events. Intrusion rating metrics (IOCs) combined with anonymous malware and C&C traffic are classified to reduce interference and save reaction time.
Integrate with your Security System
Simple connectivity and a powerful API
Powerful APIs designed to complement traditional security solutions (network security, endpoint security, and management systems) and optimize existing security operations center with the process. react to the event. Push rules against next-generation firewalls, sends intrusion event information to SIEM (Security Information Event Management) solutions, interoperability capabilities integrated with IPS (Intrusion Prevention Systems), and sends token recognition anonymous anonymous SWGs (Secure Web Gateway).
Block out
Proactively block known malicious objects and network traffic
Lastline’s platform supports existing enterprise security solutions, such as new generation firewalls (NGFW) or intrusion prevention systems (IPS), to provide information analytics and anti-intrusion capabilities. in response to the fact when there is more information about the threat’s behavior and content.
Quick response for unknown subjects
In case of a malicious, unknown zero-day attack detected by Lastline, the sensing device integrates with 3rd party security systems to create rules to prevent the ongoing attack.
Copyright © 2016 Lastline, Inc. All Rights Reserved.

VIETNET Distribution JSC hiện đang là nhà phân phối chính thức của Lastline tại Việt Nam.